As the use of technology develops, more and more devices must be managed within the scope of IT environment. If an organization neglects the devices in use, security problems could arise that lead to system downtime or data theft. To ensure stability and security, organizations need to monitor all devices they own. However, it is simply impossible for one person to monitor, say, an organization that has 100 devices that need to be monitored 24 hours a day and catch security gaps before problems even occur. Therefore, there is a need for centralized monitoring that can help monitor, namely by using SIEM which can help the organization.
But first, we need to know what is SIEM? Security Information and Event Management (SIEM) is a centralized security monitoring technology that utilizes Security Information Management (SIM) and Security Event Management (SEM) technology so that SIEM can detect threats and suspicious activity.
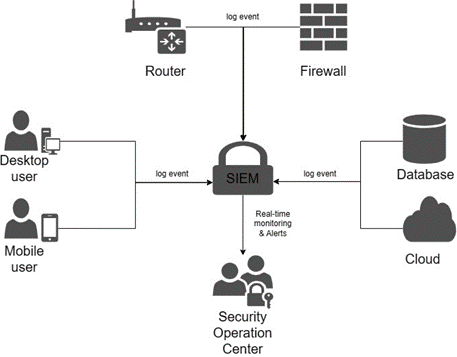
The use of SIEM is used in the dashboard display where security can be monitored in real-time against several sources within the IT Environment. IT Environment sources such as User Endpoints, network devices, software installed on devices, and other sources. The SIEM centralized dashboard can help track every active IT Environment and register every connected device which the Security Operation Center team can see in a real time.
The main focus of SIEM is on identifying the collection of each activity produced within the IT Environment. SIEM then rigorously assesses these activities to discern whether they are normal procedures or pose potential security threats. In the event of a potential threat, SIEM immediately issues an alert, providing organizations with notifications to respond quickly to emerging threats. Additionally, SIEM has detailed reports on security breaches along with relevant device information. These reports also provide an audit trail in chronological order for organizations to know what happened regarding security breaches. These reports can help organizations achieve alignment with their internal policies for security standards.
SIEM can help your organization provide real-time monitoring, rapid incident detection, centralized visibility, and efficient incident response capabilities. This will enable organizations to quickly identify and mitigate security threats, reduce incident response times, increase compliance efforts with security policies, and protect critical assets. Without a SIEM, organizations face the risk of delayed incident detection, longer wait times for attackers, reactive incident response, and potentially disrupting the operations of all departments. If you have any questions then don’t hesitate to contact us. Truslogic is ready to provide consultation that can help your organization use SIEM according to your organization’s requirements.
by : Rico Yusuf