Have you ever heard the suggestion to change your password regularly? There are many ways that hackers can use to gain access to an account, such as the brute force password generator method or the possibility that your credential data has been spread on the internet. Apart from personal accounts, companies must protect the accounts they have, especially privileged accounts. Privileged accounts are accounts that have special access rights such as user administrator, super administrator, root and so on. The consequences that can arise if a privileged account falls into the wrong hands is it can be misused by internal or external parties, being infiltrated by malware on the server, important data theft, and the server going down. Risks can also occur if privilege accounts are used together.
So, companies need to manage privileged accounts to achieve security compliance. The solution for managing access to privileged accounts from threats and cyberattacks is using Privileged Access Management (PAM). PAM is a security system that has the ability to monitor, detect and prevent accidental access or misuse when accessing critical asset resources. The PAM application is a preventive step taken by organizations to protect themselves from unauthorized access and credential theft by securing privileges on services, applications, root and administrator accounts in the system. By using PAM, it can be ensured that access is granted and executed only by authorized individuals, and access made by users will be recorded for audit purposes.
PAM works by storing privileged account credentials in a vault. The system administrator will set policies regarding what credentials can be accessed by PAM users and will be given a time limit when users access the credentials. After completing their task, the password rotation process can be done automatically. All users activities are saved and can be used as a report to make the monitoring process easier.
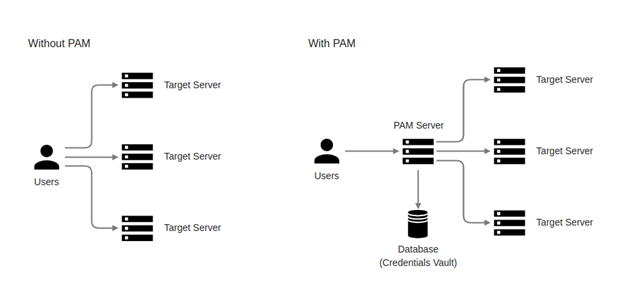
Before using PAM, users access the target server directly and need to know then enter the credentials of the target server they want to access.
After using PAM, user accesses the target server via PAM and the user only needs to use credentials to log in to the PAM console. For launching sessions to the target server, users no longer need to enter credentials because the credentials will be automatically filled in by PAM.
The following are some of the benefits of using Privileged Access Management :
- Centralized and securely encrypted storage of credentials.
- Full control over all session launches, access requests, monitoring, recording.
- The process of users moving between servers becomes efficient.
- Limited privileges for user, application, and process can reduce entrances against internal or external threats.
- Credential password rotation stored in PAM will be scheduled and done automatically, achieving security compliance.
- The privileged account password can be changed on a scheduled basis.
- Activity logs and audit helps to monitor and detect suspicious activity due to unauthorized access or malware attacks.
Companies need to protect privileged accounts to prevent data breaches. PAM solutions are required by companies for the management and security of privileged accounts to prevent unauthorized access and misuse of critical company assets by users. Truslogic is ready to help you provide consultation and support for implementing PAM solutions. Let’s Secure Together.
by : Bryan Alexis